
Relativity, the well-known eDiscovery platform, has launched an invite-only bug bounty programme as part of Relativity Trust, the company’s campaign to secure its code and platform. Researchers can gain up to $3,000 for finding critical security flaws.
Researchers will be given complete administrative access to their own workspace within the current version of RelativityOne and about 700 documents of test data to evaluate, said Relativity Chief Security Officer, Amanda Fennell, during the 10th annual Relativity Fest – the company’s conference.
One US-based expert told Artificial Lawyer: ‘I have never heard of a legal tech company involved with Bug Bounties. I would think most of them would be too concerned about the negative press of public bug finding. But it’s an interesting idea.’
However, Relativity clearly believes it’s better to be ‘out in front’ of such issues and leading the way, rather than be seen to be passive and waiting for issues to crop up.
Artificial Lawyer spoke to Relativity’s Calder7 security team about the wider challenges they face with a platform that contains sometimes extremely sensitive client information that may be part of an investigation exercise or eDiscovery process.
Tyler Young, Head of Cyber security at Relativity, told this site that they use a variety of techniques to prevent attacks and hacks on their platform, including AI to help free up the expanding team’s time.
‘We use machine learning for threat hunting, as it can learn anomalies. For example, the system can learn what is unusual, such as a log in from China, then five minutes later a log in from the US. The idea is to spot strange behaviour,’ he explained.
He added that if humans alone are checking the flow of activity they may miss small anomalies that the machine learning software will spot.
However, he said that one of the biggest risks to security remains people making naive errors when it comes to opening emails.
Interestingly, the Calder7 team tests out the company’s staff by sending them fake emails to see if they will open them and click on links.
‘Phishing emails is one of the biggest ways to attack a company. In most security situations a person is the weakest link. But our security awareness programme sends out emails [to test them], for example we sent out some fake RelativityFest emails with strange links. We’re testing to see if people will ask: ‘Why was this sent to me?” he explained.
Young added that the company’s desktops also have a special ‘report phish’ button so that anything even vaguely suspicious can be quickly sent to the cyber team.
Getting a bit more cloak and dagger, Young said that they also think about the motivations attackers may have. Could there be a nation state trying to get into the platform for a particular reason? And what methods might they use? These are questions they regularly ask themselves and then seek to prepare for.
Fundamentally they focus on what has become known as the Lockheed Martin Kill Chain – which is a methodology developed by the US arms manufacturer to predict how a hacker may operate and then stop that from happening (see the steps below).
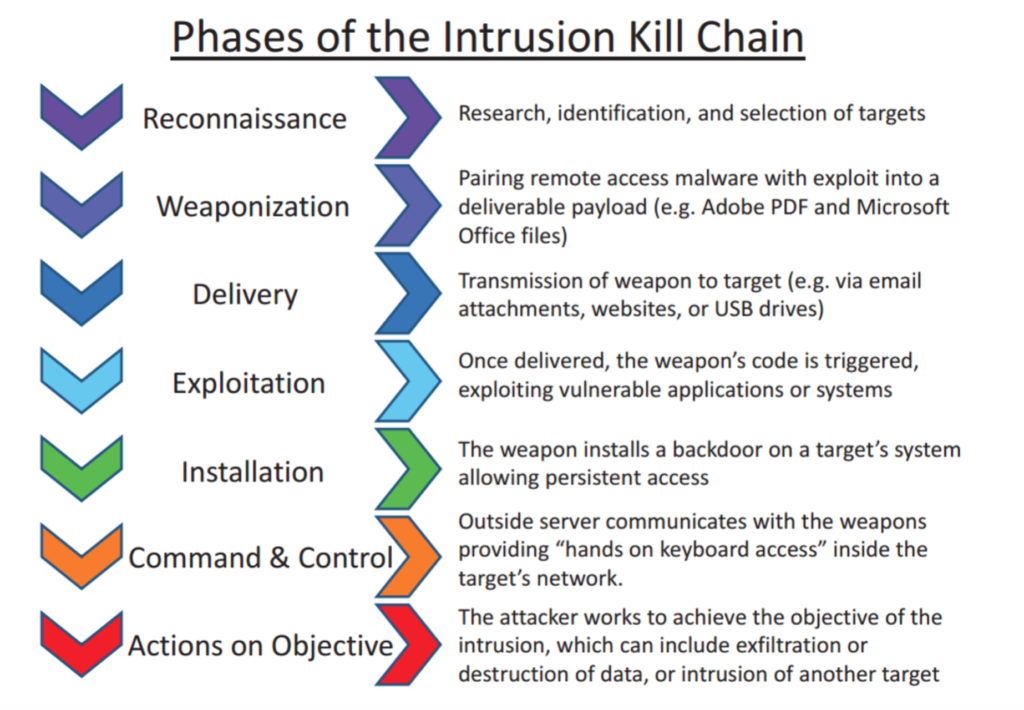
Young also said that when it came to high stakes hacking, people making a concerted effort to gain access will even do things such as drop USB keys outside the front entrance of the company they want to hack. The hope is that – despite all the risks and warnings – someone will pick it up and insert it into a device connected to the company.
When asked if Relativity is regularly under attack, Young was understandably not willing to go into details, but concluded: ‘Does Relativity get attacked? Yes. Every company does.’
He added: ‘You need to meet security standards, but it starts as a hygiene thing and then you have to keep investing to be on the cutting edge and spend on training.’
And Relativity is certainly doing that.
—
If you are interested in applying for Relativity’s bug bounty programme, please contact: Gotbugs@relativity.com
